Hackers have obtained a digital certificate good for any Google website from a Dutch certificate provider, a security researcher said.
Criminals could use the certificate to conduct "man-in-the-middle" attacks targeting users of Gmail, Google's search engine or any other service operated by the Mountain View, Calif. company.
"This is a wildcard for any of the Google domains," said Roel Schouwenberg, senior malware researcher with Kaspersky Lab, in an email interview Monday.
"[Attackers] could poison DNS, present their site with the fake cert and bingo, they have the user's credentials," said Andrew Storms, director of security operations at nCircle Security.
Man-in-the-middle attacks could also be launched via spam messages with links leading to a site posing as, say, the real Gmail. If recipients surfed to that link, their account login username and password could be hijacked.
Details of the certificate were posted on Pastebin.com last Saturday. Pastebin.com is a public site where developers -- including hackers -- often post source code samples.
According to Schouwenberg, the SSL (secure socket layer) certificate is valid, and was issued by DigiNotar, a Dutch certificate authority, or CA. DigiNotar was acquired earlier this year by Chicago-based Vasco, which bills itself on its site as "a world leader in strong authentication."
Vasco did not reply to a request for comment.
Security researcher and Tor developer Jacob Applebaum confirmed that the certificate was valid in an email answer to Computerworld questions, as did noted SSL researcher Moxie Marlinspike on Twitter. "Yep, just verified the signature, that pastebin *.google.com certificate is real," said Marlinspike.
Because the certificate is valid, a browser would not display a warning message if its user went to a website signed with the certificate.
It's unclear whether the certificate was obtained because of a lack of oversight by DigiNotar or through a breach of the company's certificate issuing website.
Schouwenberg urged the company to provide more information as soon as possible.
"Given their ties to the government and financial sectors it's extremely important we find out the scope of the breach as quickly as possible," Schouwenberg said. The situation was reminiscent of a breach last March, when a hacker obtained certificates for some of the Web's biggest sites, including Google and Gmail, Microsoft, Skype and Yahoo.
Then, Comodo said that nine certificates had been fraudulently issued after attackers used an account assigned to a company partner in southern Europe.
Initially, Comodo argued that Iran's government may have been involved in the theft. Days later, however, a solo Iranian hacker claimed responsibility for stealing the SSL certificates.
Kaspersky's Schouwenberg said "nation-state involvement is the most plausible explanation" for the acquisition of the DigiNotar-issued certificate.
"For one [thing], there's the type of information being looked for -- from Google users," said Schouwenberg. "This hints towards an intelligence operation rather than anything else. Secondly, this type of attack only works when the attacker has some control over the network, but not over the actual machine."
Others were more skeptical because of the claim that a single hacker pulled off the Comodo heist.
"I think it might still be a stretch to attribute this to the Iranian government," said Marlinspike on Twitter shortly before 4 p.m. ET. "We all know how that went last time."
The google.com certificate has not yet been revoked by DigiNotar -- the first step to blocking its use -- even though it was issued July 10.
Last March, browser makers, including Google, Microsoft and Mozilla, rushed out updates that added the stolen Comodo certificates to their applications' blacklists.
Storms said he expected Google to quickly update Chrome, and that Microsoft, Mozilla and other would do the same some time later. "I suspect that if asked [Microsoft and Mozilla] will also issue updates, as there is already a precedent," said Storms.


 drive after he has given it to someone. He wanted to get the usernames of the accounts where the pendrive was used. I thought for a while and told him that he can achieve this feat either by using Trojans or a combination of Batch and Autorun files. However,you must advise users to not to format the pendrive in order for this to work.The second option of Batch files was easy and less suspicious.So Here is how I made it possible to get the usernames when the pendrive was plugged into the PC -
drive after he has given it to someone. He wanted to get the usernames of the accounts where the pendrive was used. I thought for a while and told him that he can achieve this feat either by using Trojans or a combination of Batch and Autorun files. However,you must advise users to not to format the pendrive in order for this to work.The second option of Batch files was easy and less suspicious.So Here is how I made it possible to get the usernames when the pendrive was plugged into the PC - 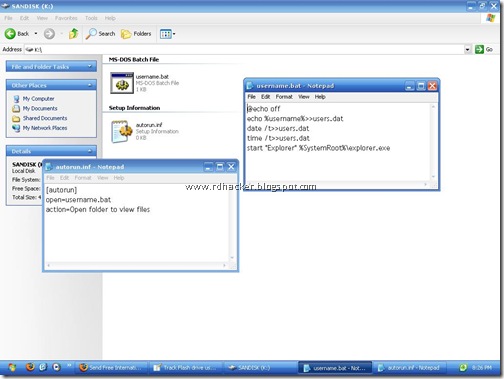
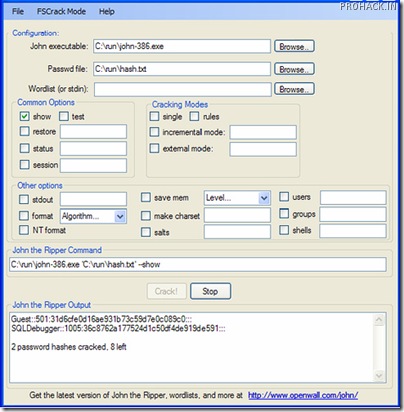
 testing and breaking program available. JTR, as its fondly called ,combines multiple password cracking packages into one package,includes auto detection of hashes and is a fast password cracker. It is currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS and supports 15 different platforms . Its primary purpose is to detect weak Unix passwords ( no..I m kidding,Its primary purpose is to break passwords :P ).It can natively detect and crack various encrypted password formats including several crypt password hash types most commonly found on various Unix flavors (based on DES, MD5, or Blowfish), Kerberos AFS, and Windows NT/2000/XP/2003 LM hash. JTR has an active community and multiple third party patches have been added to increase its functionality to include MD4-based password hashes and passwords stored in LDAP, MySQL and others unsupported hashes. JTR is the penultimate when it comes to password cracking in windows (Cain and Abel is the ultimate :P), but for Linux and open source,its the best you can get your hands on.Fire it up with a wordlist and you are good to go
testing and breaking program available. JTR, as its fondly called ,combines multiple password cracking packages into one package,includes auto detection of hashes and is a fast password cracker. It is currently available for many flavors of Unix, Windows, DOS, BeOS, and OpenVMS and supports 15 different platforms . Its primary purpose is to detect weak Unix passwords ( no..I m kidding,Its primary purpose is to break passwords :P ).It can natively detect and crack various encrypted password formats including several crypt password hash types most commonly found on various Unix flavors (based on DES, MD5, or Blowfish), Kerberos AFS, and Windows NT/2000/XP/2003 LM hash. JTR has an active community and multiple third party patches have been added to increase its functionality to include MD4-based password hashes and passwords stored in LDAP, MySQL and others unsupported hashes. JTR is the penultimate when it comes to password cracking in windows (Cain and Abel is the ultimate :P), but for Linux and open source,its the best you can get your hands on.Fire it up with a wordlist and you are good to go